Data Data Data .....! lets look at ourselves what we are doing over the internet. we simply exchanging the data over the internet yes or NO ?? Data can be in any formats. whethers it's in text , image , video , music all these are data . what we call as internet is simply a network in which we sharing our data with each other Right. whether we are chatting with someone , or putting stories and post over the instagram we are simply sending or receiving data formats over the internet.
 |
common used Data formats - video,sound,text,etc |
so now the question is why we need encyption , what is the use of encryption and decryption while we are sending or receving that much amount of data over the internet..
so the answer for this question is Data privacy .whether its our personal data ( personal chats, photos ,videos , text etc ) and or bank details ( such as credit no , internet banking username and password) or while purchasing something from any ecommerce site . so what we are doing at the time of purchase we are sharing our sensitive data with them in order to complete our purchase. So here we don't want any third person come in our network and see what kind of information we are sharing with that ecommerce site. Right why i am saying this Because nowdays its become very easy for hacker or attackers to spy on any network.and can see what kind of information we are sharing over the network. so here comes the concept of encryption.
 |
| An open network vs encrypted network |
Before i am gonna tell you what the encryption means lets first talk about a historial story which is related to encryption this story gives you an anlogy of what is encryption means ??
 |
statue of julius caesar |
you all heard the name julius caesar if you don't Julius Caesar was a Roman general and politician who played a important role in the events that led to the demise of the Roman Republic and the rise of the Roman Empire. In 60 BC so whenever be julius caesar had to convey some confidential information so he used to wrote a letter in cipher text. so in order to read the actual text that person should know caesar cipher technique in order to decipher and read actual meaningfull information. so now the question which is revolving in your mind is that what is cipher text ? right so cipher is a text which is generated through some mathmatical calculation or by an alogorithm which is meaningless for the person who don't know about that mathmatical calculation or alogorithm so in order to decipher that text a person should know about that mathmatical technique or algorithm in order to generate meaningfull text . Below is the image of caesar cipher technique
.
 |
caesar cipher technique |
so what actually julius cipher do in their confidential lettter is that as you can see above a image of alphabets so here julius caesar replaces the actual alphabets of letter with the third shift of alphabet in alphabatical oder for example if actual text which he wants to send contains 'A' alphabet then he wrote it is D which is three steps forward in the alphatical order similary if the alphabet is ' c' then he wrote it ' F' . so this shifting of elements is knows as caesar cipher name after julius caesar. and this is what cipher text look like . so if any third person which don't know cipher technique and the no of shift which is used by julius caesar convert it into cipher is unable to decipher it . In above image he used three shift . which is also knows as key so inorder to decipher the julius caesar letter you have the knowledge of cipher technique and the key used by her.
Now the actual question is what is encryption
in simple words converting a plain text into cipher text this process is known as encryption above story is the very simplest example of how encryption look like.
for example we have Triple DES , RSA , Blowfish , Twofish , AES encryption alogorithms.
and to convert cipher text into a plain text this process is known as decryption.
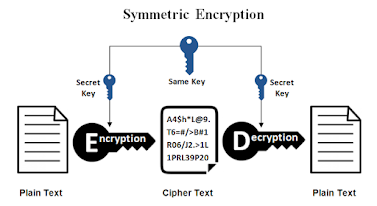
There are two types of encryption Methods
1 - symmetric encryption
2 - Asymmetric Encryption
 |
| img source : ssl2buy.com/wiki |
Asymmetric Encryption is little bit different from symmetric encryption. so in asymmetric encrytption we have two keys first is public key and second is our private key .so first lets talk about public key - public key is a key which we can share with anybody so if any person wants to share me something then that peroson have to use my mine public key in order to encrypt that data for me .Once that encrypted data reaches me then i have to use mine own private key in order to decrypt that encrypted data. we don't share our private with anybody it only for our use.




0 Comments